Every businesses goal is to have a thriving business, that not only makes money but serves its clients through a vision set forth by the company. These goals not only define the company today but will help guide the growth and future of the company.
Analytics/Analysis
Content Based Marketing
Traditional marketing is becoming less and less effective by the minute. With so many people living busy lives, and managing a million things it makes it more important than even to grab your audience’s attention and leave them wanting more. You may be asking yourself how do I do that?
SMB Privacy Security Laws
By Gary Audin
“Customer Privacy and Security; MSP Liabilities?
The MSP manages customer resources. The MSP may also manage security for its customers. If the security is breached and consumer data is released does the MSP have liability? Possibly!
Pandemic and Beyond
During any disaster or pandemic, such as COVID-19, MSPs must prepare for disruption in their business as well as prepare to protect their customers and clients vital IT services. As many of you know MSPs are one of the most important players for many businesses not only during the pandemic,
What is the Future of Office Space?
The pandemic has forced the adoption of new ways of working. From working at home, to social distancing at the office, organizations are having to reimagine not only their office space, but also how to create safe, productive, and enjoyable jobs and lives for employees. Before the pandemic, the conventional wisdom
Dharma Virus
Our virus duo (Michael Jenkin and Ken Dwight) take over SMB Nation to chat about the new developments in the malware and security field. These two explore a virus that has been around since 2016 and has been reappearing with new versions regularly during recent years.
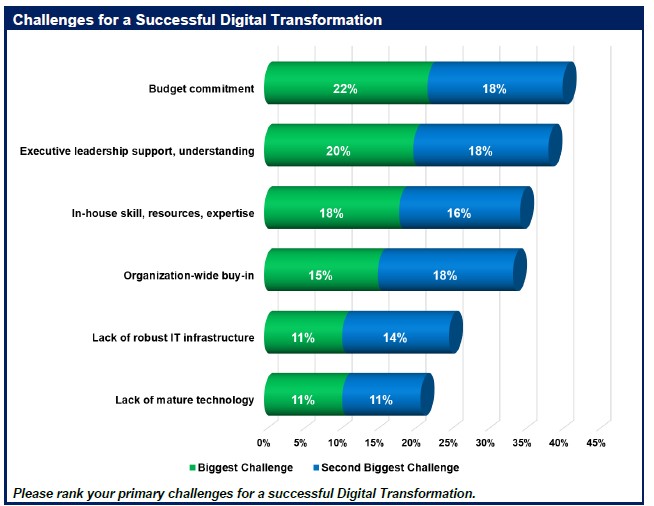
SMB Dig Trans Challenge
By Gary Audin
Digital transformation is not just technology, not just a tool, not just an application. It is a change in doing business.